Instructions for FLASH encryption function¶
1. Purpose of FLASH encryption¶
The purpose of FLASH encryption is to prevent the products developed by application developers from being copied by poor manufacturers through FLASH. If this is not the purpose, there is no sense in using this encryption function. After using this encryption function, if the FLASH firmware is COPY to another FLASH, it will prompt that the verification failed (you can also customize other processing methods).
2. Encryption methods supported by SDK¶
The SDK supports two encryption methods. One is user defined encryption algorithms, which are provided to upgrade tools and SDK calls. This method allows users to keep their encryption algorithms confidential, with higher security, but also relatively large complexity and workload. The other is that the SDK comes with its own default encryption algorithm. Users only need to enter the same password in the upgrade tool and SDK. It is easy for users to use.
2.1. Default Encryption Algorithm¶
This encryption method is simple to use, with small user development and low security requirements.
2.1.1. SDK related modifications¶
- Modify user_ config. h. Enable encryption function, COPYRIGHT_ VERIFICATION is defined as 1;
- Modify user_ config. h. Set encryption mode, ENCRYPT_ ALGORITHM is defined as ENCRYPT by default_ DEFAULT;
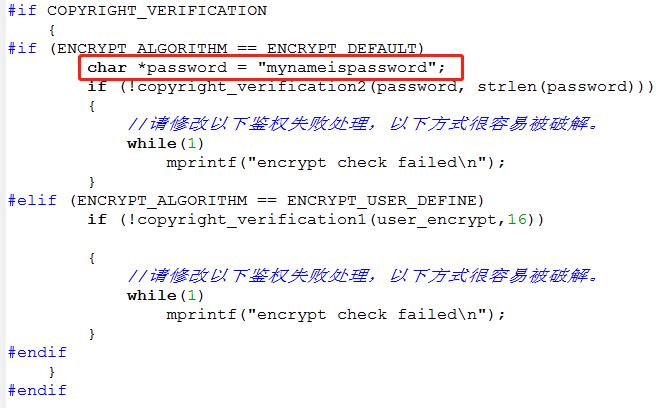
- Modify ci_ flash_ data_ info. c. In function ci_ flash_ data_ info_ In init, copyright_ Before verification2 is called, change the encryption password to your own password, as shown in the following figure;
- Modify ci_ flash_ data_ info. c, copyright_ After verification2 is called, the verification failure is handled. The sample code in the SDK keeps printing the verification failure information in an endless loop. It is recommended that you modify this method, because this prompt method is easy to be cracked by reverse engineering.
2.1.2. Use of Upgrade Tool¶
-
When updating the firmware with the upgrade tool, select “standard encryption” as the encryption algorithm and fill in the password.
-
Open the serial port to upgrade normally.
2.2. User defined encryption algorithm¶
This encryption method is a little more complicated to use. The user development volume is a little larger. Customers with higher security requirements can use this method.
2.2.1. User defined encryption algorithm interface¶
(1) C++interface:
//Psrc: source data buffer
//src_ Len: Source data length
//Pdst: output buffer for saving encryption results
//dst_ Len: output buffer size
//out_ Len: Length used to output result data
//Note: If pdst is NULL, only the length of the result data will be calculated
bool func(char *psrc, int src_len, char *pdst, int dst_len, int *out_len)
(2) Python interface:
def encrypt(data):
out_ data = your_ Encrypt (data) # Sample code. Users need to modify it to their own algorithm
return out_ data
2.2.2. SDK related modifications¶
- Modify user_ config. h, COPYRIGHT_ VERIFICATION is defined as 1;
- Modify user_ config. h, ENCRYPT_ ALGORITHM is defined as ENCRYPT_ USER_ DEFINE;
- Write a user-defined encryption algorithm function according to the interface provided by the user-defined encryption algorithm interface in Section 2.2.1;
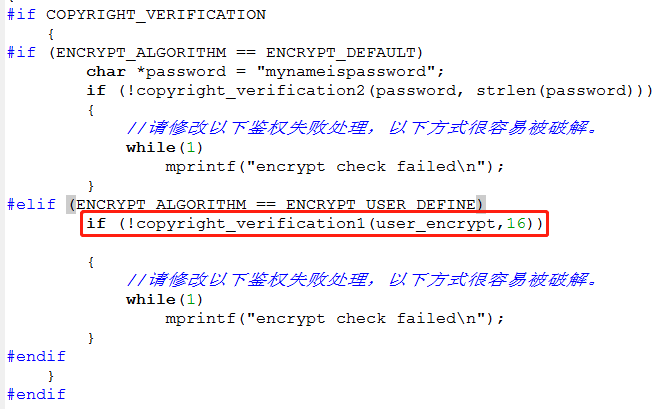
- Modify ci_ flash_ data_ info. c. In function ci_ flash_ data_ info_ Init, call copyright_ When verifying 1, modify the parameters and pass in the user-defined encryption function, as shown in the following figure;
- Modify ci_ flash_ data_ info. c, copyright_ After verification1 is called, the verification failure is handled. The sample code in the SDK keeps printing the verification failure information in an endless loop. It is recommended that you modify this method, because this prompt method is easy to be cracked by reverse engineering.
2.2.3. Use of upgrade tools¶
- Write a custom encryption algorithm function according to the interface given by the custom encryption algorithm interface in Section 2.2.1. The current upgrade tool supports the following call methods: C++dynamic link library (. dll);
-
When updating the firmware with the upgrade tool, select “standard encryption” as the encryption algorithm and fill in the password.
-
Open the serial port to upgrade normally.
3. Applicable environment¶
Each FLASH chip must have a unique id.